Keeping your [PSADT] packages safe
How is InstAlladdin protecting the Powershell App Deployment Toolkit template?
InstAlladdin is hashing the whole Powershell App Deployment toolkit template folder and checking its integrity before using it to create any package.
What is hashing?
Hashing is a data structure that stores information in an unordered, non-linear format. It works by taking a string of characters or other data and converting it into a “hash” value using a mathematical algorithm. The hash value is then used as the key to store the corresponding data in the database or other data structures.
What is a hash value?
A hash value is a unique, fixed-length output generated by a one-way hashing algorithm. This output is also known as a "message digest" or "fingerprint". Hash values are commonly used to verify the integrity of digital data, for example when downloading files from the internet. They can also be used to create digital signatures.
Which hashing algorithm is the InstAlladdin software using?
InstAlladdin is using SHA-256 hashing algorithm. SHA-256 is a cryptographic hash algorithm used by many modern applications and websites to secure data. It produces a 256-bit (32-byte) fixed size output that acts as a digital fingerprint of the data it was provided with. SHA-256 is an industry standard and is one of the strongest hashing algorithms available, making it difficult to break.
Some other common algorithms are for example MD5 and SHA1. InstAlladdin is not using any of them, because both have been attacked. Due to the engineering hash collisions that have been discovered and made technically insecure, it is not advised to trust either MD5 or SHA1 algorithms for hashing passwords or data.
How it works
At each start and before generating each PSADT package, InstAlladdin is performing a verification if the hash value of the PSADT template folder has not been changed. Any modification will lead to drastic variations in the hash value.
For example, the SHA-256 hash of the original PSADT template (of the whole folder), is:
D88726C1CB975336A2C9EFC6F6E5A130898C737BC490E94C786A952749446843
If we add this text (## Execute some malicious code) to line 148 in the Deploy-Application.ps1 file, the SHA-256 hash value of the template folder changes to:
5B622362312565A79C15C5B9B1A846D9A2CC52564E6E25C4C6A8E32286259D30
Hands-on Guide
Install InstAlladdin
Follow the steps below to install InstAlladdin software.
In MS Windows click the Start button.
In the menu panel that appears find Microsoft Store and open it.
In the Microsoft Store search for the InstAlladdin application.
It looks like shown below.
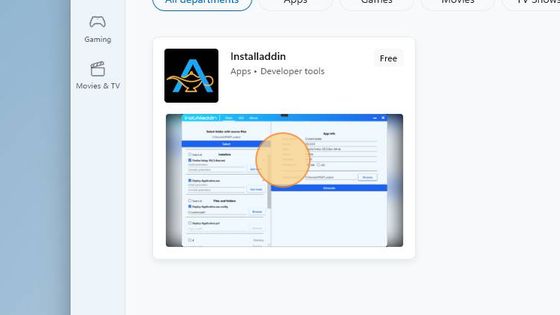
Click on the InstAlladdin application listing.
Click on the Install button.
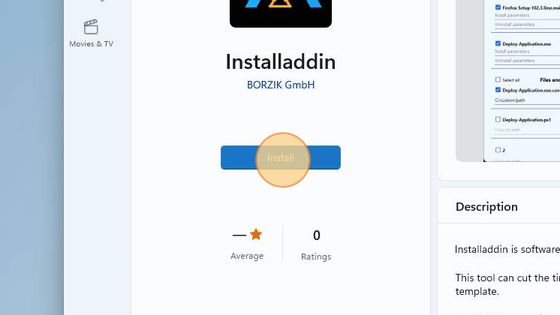
When the installation is complete, the button text will change to Open. Click it to open InstAlladdin.
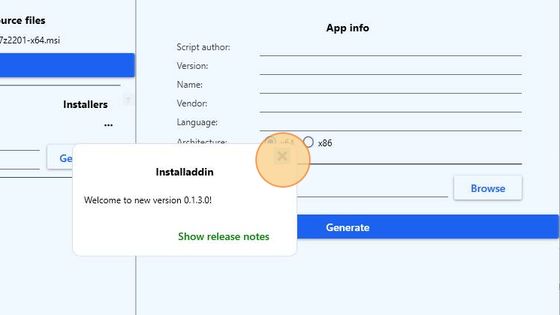
A notification about the current software version will appear once at the first start of a new version.
Upon its start the application copies the Powershell App Deployment Toolkit template to: C:\ProgramData\Installaddin.
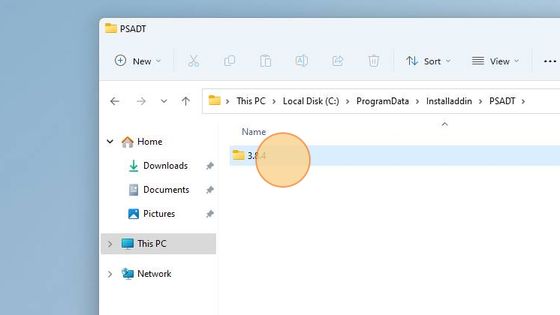
Open the File Explorer and navigate to the C:\ProgramData\Installaddin location.
The Powershell App Deployment Toolkit template is located in the C:\ProgramData\Installaddin\PSADT\3.8.4 folder; “3.8.4” represents PSADT version and will be updated as soon as new PSADT will be released.
Download PSAppDeplyToolkit
Download the PSAppDeployToolkit from its original source, so you can compare it with the version that the InstaAlladin application provides.
Open a Web browser (e.g. Firefox) and navigate to psappdeploytoolkit.com. Click on the Download menu item.
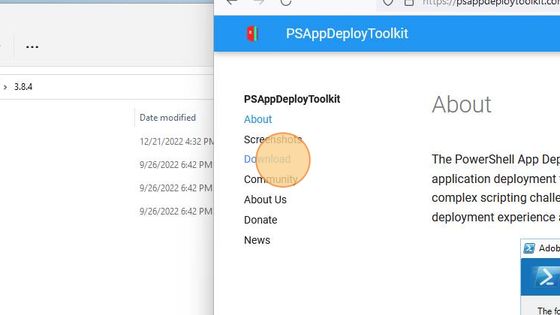
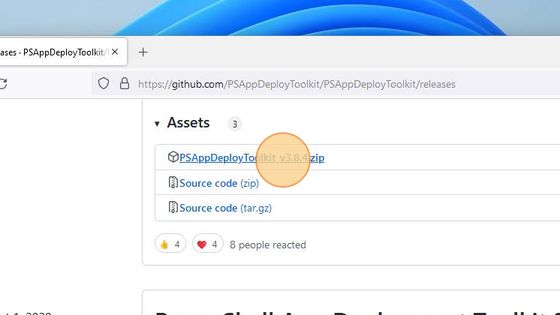
You will be redirected to the GutHub page with the official Repository of Powershell App Deployment Toolkit. On this GitHub page, scroll down to the Assets section and click on the PSAppDeplyToolkit_v3.8.4.zip to download it.
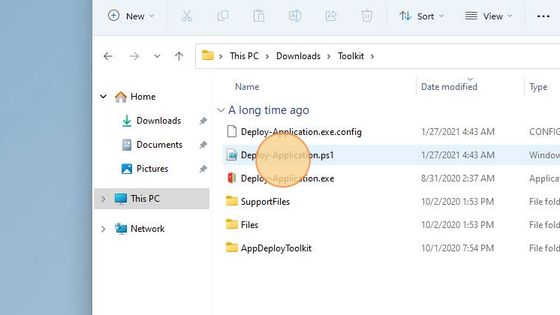
After the download is completed, extract the archive contents in a convenient location.
Comparison
Now we are going to compare the template which is included in InstAlladdin and the one, which we have just downloaded from the PSADT repository and extracted into the local Downloads folder.
First, we open the Deploy-Application.ps1 file from the template which we have just downloaded in Notepad++.
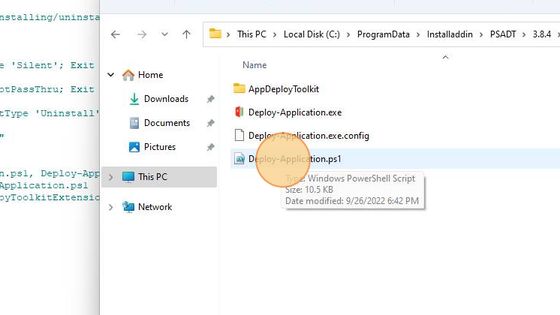
After that, we open the Deploy-Application.ps1 file that is included in InstAlladdin software, located in C:\ProgramData\Installaddin\PSADT\3.8.4.
We will use Notepad++ to open that file as well.
We will compare both files in Notepad++ using the Compare Plugin.
Note: You can use software of your choice to make the comparison.
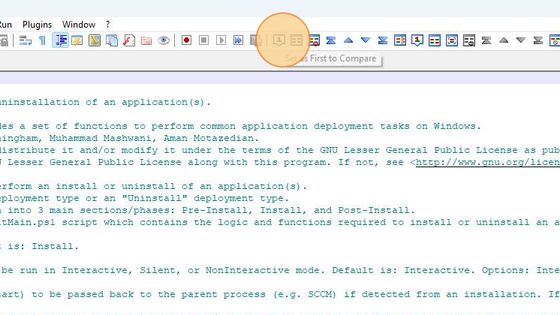
In Notepad++ we click on the first open file’s tab and then click on the Set as first to Compare icon.
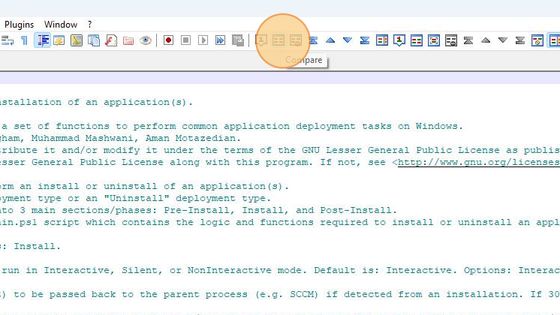
Afterwards, we click on the second open file’s tab and then click on the Compare icon.
The comparison shows that both template files match.
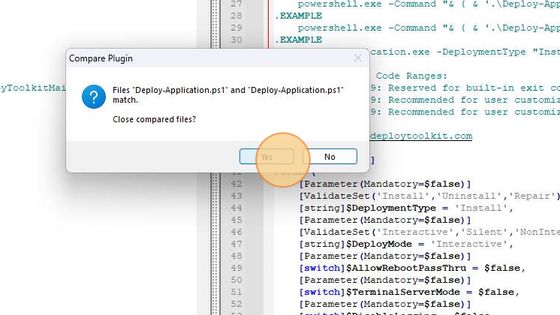
The official Powershell App Deployment Toolkit template exactly matches the one included in InstAlladdin.
InstAlladdin Operation Security
The following steps describe the operation of InstAlladdin and demonstrate its security mechanisms to prevent creation of packages with undesired or malicious elements.
Note: The 7-Zip X64 MSI installer is used in the test scenario below. If you want to follow the steps in this test scenario, you can download the installer here.
Start InstAlladdin via Windows Start menu / All applications.
Select folder with source files
Click the Select button to browse and load the 7z2201-x64.msi file. It will appear in the Installers section of the application.
Installers
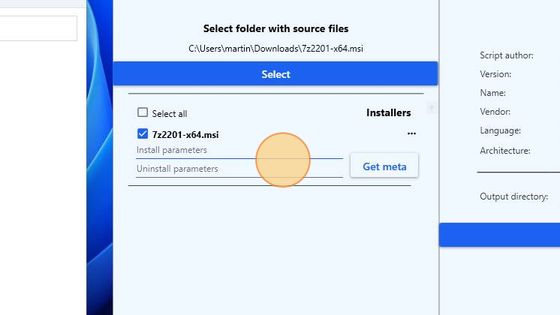
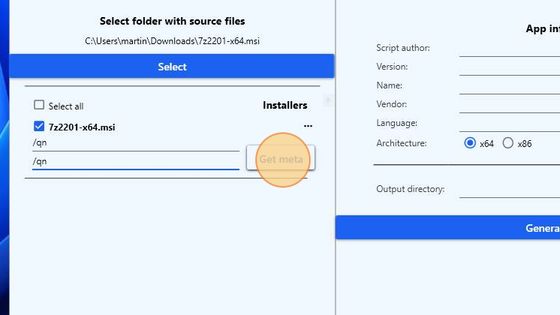
In the fields for the Install and Uninstall parameters enter: “/qn”.
Click the Get meta button.
App info
The metadata will be automatically retrieved and populated for the installer selected.
In the Script author field enter your name.
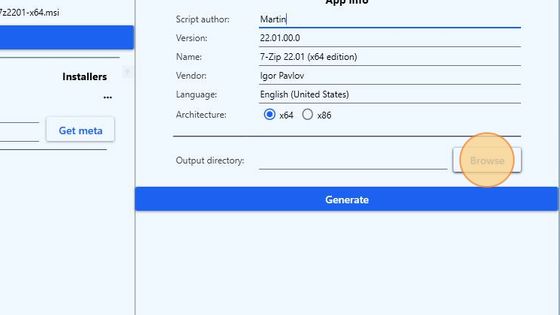
Under the loaded metadata, mark the corresponding architecture of the selected installer file; x64 in this case.
Click the Browse button to select an output folder for the generated package script.
Manipulate the Template
Navigate to the C:\ProgramData\Installaddin\PSADT\3.8.4 folder. Open the Deploy-Application.ps1 file for editing.
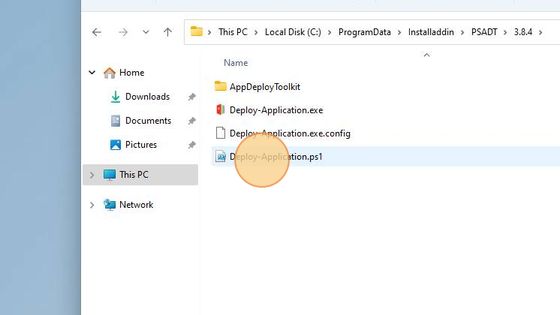
To simulate the manipulation of the template, add a comment to Post-Installation tasks in the Deploy-Application.ps1 file.
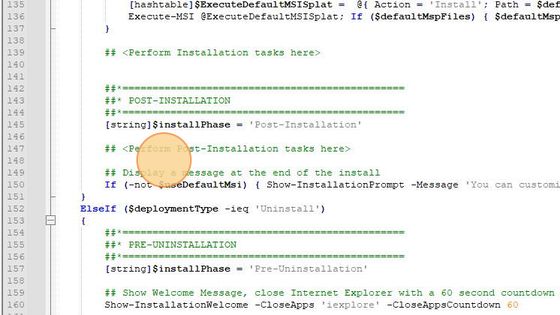
At line 148 type:
## Execute some malicious code
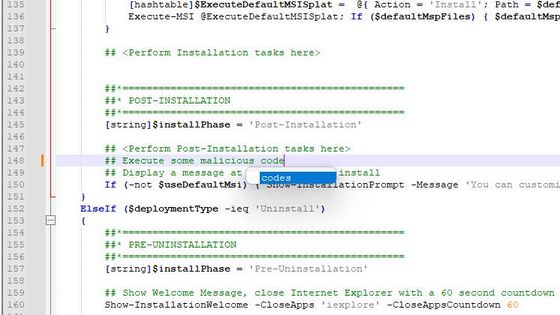
Press Ctrl+S key combination to save the changes and then close the file.
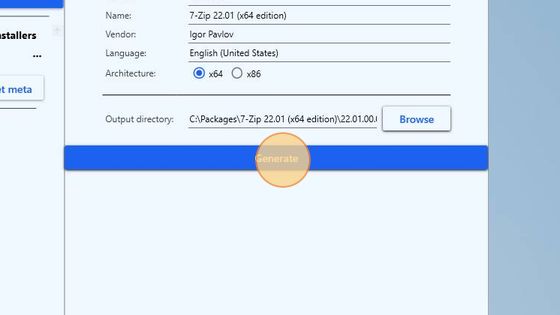
Go back to InstAlladdin with the already prepared setup and click the blue Generate button.
Security check will be performed and a popup with a warning message will appear.
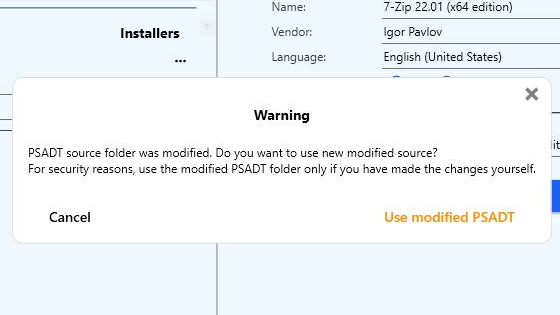
You can either accept the modified PSADT template or click Cancel.
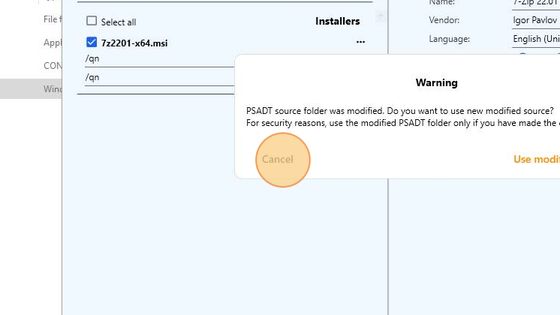
If you click Cancel, the popup with the warning will be closed, but a warning sign will appear in the lower right corner of InstAlladdin main application window.
When you click on it, the same popup with the warning message will be displayed.
Select the Use modified PSADT option only if you want to use the changed template for generating PSADT packages with InstAlladdin.
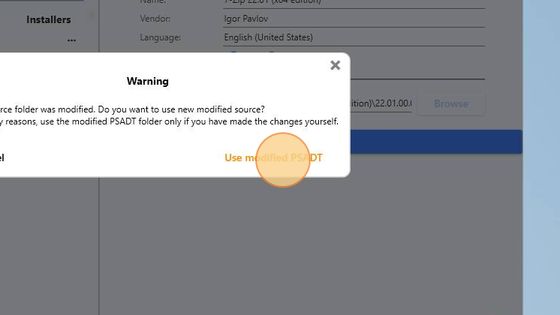
For the demonstration purposes, we will click the Use modified PSADT button.
Click the Generate button again.
When the process completes, a notification message will be displayed. It will also show the location of the generated PSADT package.
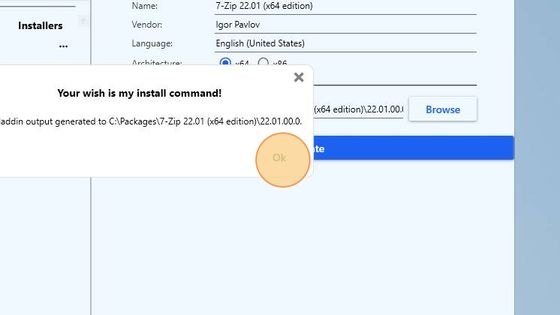
In File Manager navigate to C:\Packages\7-Zip 22.01 (x64 edition)\22.01.00.0. Open and inspect the generated installation file.
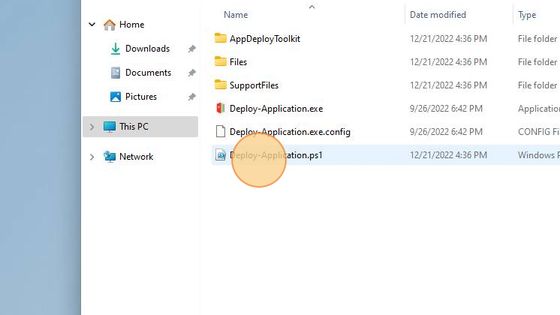
The manually added line “## Execute some malicious code” in the template is present there as well.
Note: The original Deploy-Application.ps1 template file can be recovered from the PSAppDeplyToolkit_v3.8.4.zip.
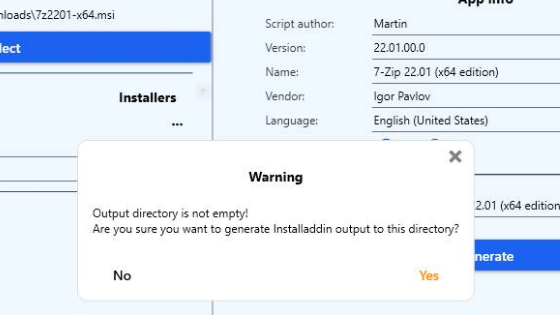
Output directory not empty
To prevent accidental replacement of existing packages, InstAlladdin will warn if you select an output directory that is not empty.
For example, if you run the generation procedure for the 7-Zip installer again, without changing the output folder first.